Hey there tech-savvy readers, ever wondered what the best remoteIoT device SSH could do for your life? In this digital age where everything is connected, securing your IoT devices has become crucial. From smart homes to industrial automation, remoteIoT device SSH plays a key role in keeping your systems safe and accessible. Let’s dive into the world of secure remote access and see how it can revolutionize the way you interact with your devices.
Imagine being able to control your smart thermostat or monitor your security cameras from anywhere in the world. Sounds cool, right? But with great power comes great responsibility. That’s where remoteIoT device SSH comes in. This technology allows you to securely connect to your IoT devices over the internet, ensuring that your data stays safe and your devices function as intended.
Now, you might be thinking, “Why do I need SSH for my IoT devices?” Well, buckle up because we’re about to break it down for you. In the next few thousand words, we’ll explore everything you need to know about the best remoteIoT device SSH options, how they work, and why they matter. So grab your favorite beverage and let’s get started!
Read also:Kylie Jenner The Rise Of A Beauty Empire And Beyond
Before we dive deep into the nitty-gritty, here’s a quick table of contents to help you navigate through this article. Feel free to jump around if you’re already familiar with some sections!
- What is SSH?
- IoT and SSH: A Match Made in Tech Heaven
- Top RemoteIoT Devices for SSH
- Why SSH is the Best Choice for IoT Devices
- How to Set Up SSH for Your IoT Devices
- Security Tips for RemoteIoT SSH
- Common Issues and Troubleshooting
- The Future of SSH in the IoT World
- Comparison of Popular RemoteIoT SSH Devices
- Wrapping It Up: Best RemoteIoT Device SSH
What is SSH? A Brief Overview
Let’s start with the basics. SSH stands for Secure Shell, and it’s like a superhero for your network connections. It’s a protocol that allows you to securely access remote devices over an unsecured network. Think of it as a secret tunnel that keeps your data safe from prying eyes. SSH encrypts all communication between your computer and the remote device, making it super hard for hackers to intercept your info.
SSH isn’t just for tech nerds; it’s for anyone who wants to protect their data. Whether you’re managing a fleet of IoT devices or just controlling your smart home gadgets, SSH can be your best friend. It’s like having a personal bodyguard for your digital life.
Why SSH Matters in Today’s World
In today’s hyper-connected world, security is more important than ever. With billions of IoT devices out there, the risk of cyberattacks is real. SSH helps mitigate that risk by providing a secure way to access and manage your devices. It’s like locking your front door when you leave the house—except in this case, the lock is unbreakable.
And let’s not forget about convenience. With SSH, you can access your devices from anywhere in the world, as long as you have an internet connection. So if you’re on vacation in Bali and you need to check on your smart fridge back home, SSH has got you covered.
IoT and SSH: A Match Made in Tech Heaven
Now let’s talk about the love story between IoT and SSH. IoT devices are awesome, but they come with their own set of challenges. One of the biggest challenges is security. IoT devices are often connected to the internet, making them vulnerable to attacks. That’s where SSH comes in to save the day.
Read also:Doja Cat The Queen Of Modern Pop And Hiphop
SSH provides a secure way to connect to your IoT devices, ensuring that your data stays safe and your devices function properly. It’s like a shield that protects your devices from the bad guys. Whether you’re managing a smart home or running an entire factory, SSH can help you keep everything under control.
How SSH Enhances IoT Security
SSH enhances IoT security in several ways. First, it encrypts all communication between your computer and the IoT device, making it nearly impossible for hackers to intercept your data. Second, it provides authentication, ensuring that only authorized users can access your devices. And third, it allows you to manage your devices remotely, without having to physically be there.
Let’s break it down with some bullet points:
- Encryption: Keeps your data safe from prying eyes.
- Authentication: Ensures only authorized users can access your devices.
- Remote Access: Allows you to manage your devices from anywhere in the world.
Top RemoteIoT Devices for SSH
Now that we’ve established why SSH is so important for IoT devices, let’s talk about some of the best remoteIoT devices out there. There are tons of options available, each with its own strengths and weaknesses. Here are a few of our favorites:
Raspberry Pi: The Raspberry Pi is a tiny but powerful computer that’s perfect for IoT projects. It supports SSH out of the box, making it easy to set up and use. Plus, it’s super affordable, so you don’t have to break the bank to get started.
ESP32: The ESP32 is another great option for IoT projects. It’s a microcontroller that supports Wi-Fi and Bluetooth, making it perfect for remoteIoT applications. It also supports SSH, so you can securely connect to your devices from anywhere.
Arduino: While the Arduino doesn’t support SSH natively, you can still use it for IoT projects by adding a Wi-Fi or Ethernet shield. With a little bit of tinkering, you can set up SSH and start managing your devices remotely.
Comparing the Top RemoteIoT Devices
Let’s take a closer look at these devices and see how they stack up against each other. Here’s a quick comparison:
- Raspberry Pi: Affordable, powerful, and easy to set up with SSH.
- ESP32: Compact, supports Wi-Fi and Bluetooth, and great for remoteIoT projects.
- Arduino: Versatile, but requires additional hardware for SSH support.
Why SSH is the Best Choice for IoT Devices
There are plenty of ways to connect to your IoT devices, but SSH stands out as the best option. Why? Because it’s secure, reliable, and easy to use. Let’s break it down:
Security: SSH encrypts all communication between your computer and the IoT device, making it nearly impossible for hackers to intercept your data. It also provides authentication, ensuring that only authorized users can access your devices.
Reliability: SSH is a proven technology that’s been around for decades. It’s reliable and works seamlessly with most IoT devices. Plus, it’s supported by a wide range of operating systems, so you can use it on just about any device.
Convenience: With SSH, you can manage your IoT devices from anywhere in the world, as long as you have an internet connection. No more having to physically be there to make changes or check on your devices.
SSH vs. Other Remote Access Protocols
While SSH is the best choice for most IoT applications, there are other remote access protocols out there. Let’s compare SSH to some of the alternatives:
- FTP: FTP is great for transferring files, but it’s not as secure as SSH.
- Telnet: Telnet is similar to SSH, but it doesn’t encrypt communication, making it less secure.
- VNC: VNC allows you to remotely control a device’s graphical interface, but it’s not as secure as SSH.
How to Set Up SSH for Your IoT Devices
Setting up SSH for your IoT devices is easier than you might think. Here’s a step-by-step guide to help you get started:
- Install an SSH server on your IoT device. Most devices come with SSH pre-installed, but if not, you can usually install it manually.
- Enable SSH on your device. This usually involves going into the device’s settings and turning on the SSH option.
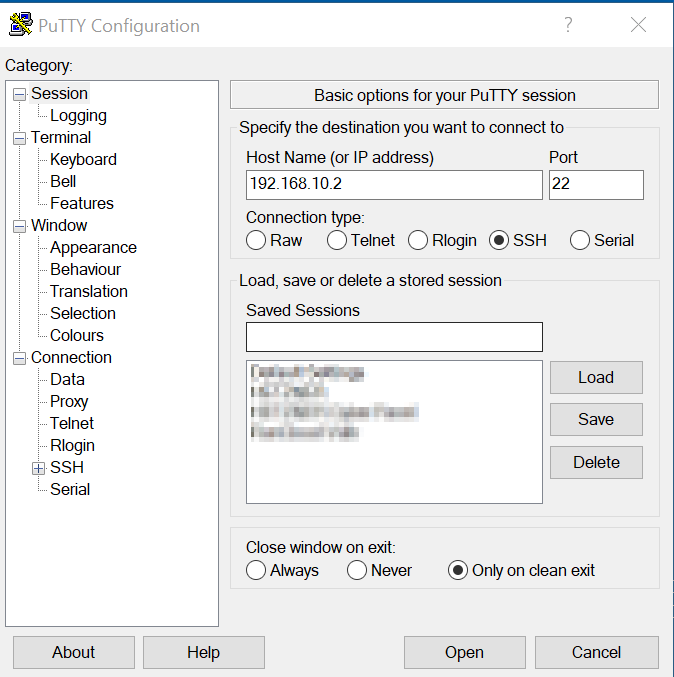
- Connect to your device using an SSH client. There are tons of SSH clients available, both free and paid. PuTTY is a popular choice for Windows users, while macOS and Linux users can use the built-in terminal.
- Enter your device’s IP address and login credentials when prompted. If everything is set up correctly, you should now have a secure connection to your IoT device.
Tips for a Successful SSH Setup
Here are a few tips to help you set up SSH successfully:
- Make sure your device is connected to the internet.
- Use strong passwords or SSH keys for added security.
- Test your connection before relying on it for critical tasks.
Security Tips for RemoteIoT SSH
While SSH is a secure protocol, there are still some things you can do to make your connections even more secure. Here are a few tips:
- Use SSH keys instead of passwords. SSH keys are much harder to crack than passwords, making them a safer choice.
- Disable password authentication. If you’re using SSH keys, there’s no need to keep password authentication enabled.
- Limit access to specific IP addresses. If you only need to access your devices from certain locations, you can restrict access to those IP addresses.
Common Security Threats and How to Avoid Them
Here are some common security threats to watch out for and how to avoid them:
- Brute-force attacks: Use SSH keys and disable password authentication to prevent brute-force attacks.
- Man-in-the-middle attacks: Use SSH’s built-in encryption to protect against man-in-the-middle attacks.
- Unauthorized access: Limit access to specific IP addresses and use strong passwords or SSH keys.
Common Issues and Troubleshooting
Even with the best setup, things can go wrong. Here are some common issues you might encounter and how to fix them:
- Connection refused: Make sure your device is connected to the internet and that SSH is enabled.
- Authentication failed: Double-check your login credentials and make sure SSH keys are set up correctly.
- Timeout errors: Try restarting your device or checking your internet connection.
Advanced Troubleshooting Tips
For more advanced troubleshooting, here are a few tips:
- Check your device’s logs for error messages.
- Make sure your firewall isn’t blocking SSH connections.
- Try connecting from a different network to rule out local issues.
The Future of SSH in the IoT World
As the IoT continues to grow, SSH will become even more important. With billions of devices connected to the internet, security will be a top priority. SSH will play a key role in keeping those devices safe and secure.
Future advancements in SSH technology will likely focus on improving performance, increasing security, and making it easier to use. We can expect to see new features and protocols that will make SSH even more powerful and versatile.
What to Expect in the Next Few Years
Here’s what you can expect from SSH in the next few years:
- Improved encryption algorithms for better security.
- Enhanced usability features for easier setup and management.
- Integration with other technologies, such as blockchain, for added security.
Comparison of Popular RemoteIoT SSH Devices
Let’s wrap things up with a quick comparison of some popular remoteIoT SSH devices:
| Device | Price | Features | Pros | Cons |
|---|---|---|---|---|
| Raspberry Pi | $35 | SSH, Wi-Fi, Bluetooth | Affordable, powerful, |