Imagine this—you’ve got a bunch of smart devices scattered all over the world, and you need to manage them remotely. Sounds like a challenge? Enter SSH RemoteIoT Example, the key to unlocking secure, reliable, and efficient connections between your IoT devices and the cloud. In today's hyper-connected world, IoT devices are everywhere, from smart homes to industrial setups. But managing these devices securely is no small feat. That's where SSH comes in, providing a secure tunnel for remote access and control. Let's dive into why SSH RemoteIoT Example is a game-changer.
SSH, or Secure Shell, is like a digital fortress that protects your data from prying eyes. When you’re dealing with IoT devices, security is not just an option—it’s a necessity. With SSH RemoteIoT Example, you can ensure that your devices are safe from hackers, data breaches, and other cyber threats. And hey, who doesn’t want that? Whether you're a tech enthusiast, a business owner, or a developer, understanding SSH RemoteIoT Example is crucial for anyone who wants to harness the full potential of IoT.
In this article, we’ll break down everything you need to know about SSH RemoteIoT Example. From setting up secure connections to troubleshooting common issues, we’ve got you covered. So, buckle up and get ready to learn how to take your IoT game to the next level!
Read also:Unveiling Virginia Lewsader A Closer Look At Her Life Career And Impact
Table of Contents
- What is SSH?
- SSH RemoteIoT Basics
- Why Use SSH for IoT?
- Setting Up SSH for RemoteIoT
- Example Implementation of SSH RemoteIoT
- Security Considerations
- Common Issues and Solutions
- Best Practices for SSH RemoteIoT
- The Future of SSH in IoT
- Conclusion
What is SSH?
SSH, or Secure Shell, is like the Swiss Army knife of network tools. It’s a protocol that allows you to securely connect to remote devices, transfer files, and execute commands—all while keeping your data encrypted and safe from hackers. Think of it as a digital handshake that ensures only authorized users can access sensitive systems.
Now, why is SSH so important? In the age of IoT, where billions of devices are connected to the internet, security is paramount. Without proper protection, your devices could be vulnerable to attacks, data breaches, and other nasty stuff. SSH provides a secure channel for communication, ensuring that your data remains private and intact.
How Does SSH Work?
SSH works by creating an encrypted tunnel between two devices. When you connect to a remote server or IoT device, SSH encrypts all the data being transmitted, making it nearly impossible for hackers to intercept or decipher. This means you can safely manage your devices from anywhere in the world without worrying about security.
Here’s a quick rundown of how SSH works:
- Authentication: You log in using a username and password or a public key.
- Encryption: All data is encrypted during transmission.
- Secure Communication: You can execute commands, transfer files, and more—all within a secure environment.
SSH RemoteIoT Basics
So, what exactly is SSH RemoteIoT Example? Simply put, it’s the process of using SSH to remotely manage and control IoT devices. Whether you’re monitoring a smart thermostat, controlling a drone, or managing an entire fleet of sensors, SSH RemoteIoT Example provides the tools you need to do it securely and efficiently.
Here’s why SSH RemoteIoT Example is so powerful:
Read also:Monica Barbaro Husband The Inside Story You Didnrsquot Know
- Security: SSH ensures that your data is encrypted and protected from unauthorized access.
- Flexibility: You can manage devices from anywhere in the world, as long as you have an internet connection.
- Scalability: SSH can handle large-scale deployments, making it ideal for businesses and organizations with thousands of IoT devices.
Key Features of SSH RemoteIoT
SSH RemoteIoT Example offers a range of features that make it an essential tool for IoT management. Here are some of the highlights:
- Remote Access: Connect to your devices from anywhere in the world.
- File Transfer: Transfer files securely using SFTP (SSH File Transfer Protocol).
- Command Execution: Execute commands directly on your devices without needing physical access.
- Authentication: Use public key authentication for added security.
Why Use SSH for IoT?
When it comes to IoT, security is the name of the game. Without proper protection, your devices could be vulnerable to attacks, data breaches, and other cyber threats. That’s why SSH is such a great choice for IoT applications. It provides a secure, reliable, and scalable way to manage your devices, ensuring that your data remains safe and intact.
Here are a few reasons why SSH is the go-to protocol for IoT:
- Encryption: SSH encrypts all data transmitted between devices, making it nearly impossible for hackers to intercept or decipher.
- Authentication: SSH uses public key authentication, which is much more secure than traditional username/password combinations.
- Scalability: SSH can handle large-scale deployments, making it ideal for businesses and organizations with thousands of IoT devices.
- Flexibility: SSH works on a wide range of platforms and devices, making it easy to integrate into your existing infrastructure.
SSH vs. Other Protocols
While there are other protocols out there, SSH stands out for its security, flexibility, and ease of use. Here’s how SSH compares to some of the other popular protocols:
- Telnet: Telnet is insecure and should be avoided for IoT applications.
- HTTP: HTTP is not encrypted by default, making it less secure than SSH.
- TLS/SSL: TLS/SSL is secure, but it can be more complex to set up than SSH.
Setting Up SSH for RemoteIoT
Setting up SSH for your IoT devices is surprisingly easy. Whether you’re working with a Raspberry Pi, an Arduino, or any other type of device, the process is pretty straightforward. Here’s a step-by-step guide to help you get started:
Step 1: Install SSH
Most IoT devices come with SSH pre-installed, but if yours doesn’t, you’ll need to install it manually. You can usually do this using a package manager like apt-get or yum.
Step 2: Configure SSH
Once SSH is installed, you’ll need to configure it to meet your needs. This might include setting up public key authentication, disabling password authentication, and configuring firewall rules.
Step 3: Connect to Your Device
With SSH configured, you can now connect to your device from anywhere in the world. Simply open a terminal or command prompt and enter the following command:
ssh username@device_ip_address
Tips for Setting Up SSH
Here are a few tips to help you set up SSH successfully:
- Use Public Key Authentication: This is much more secure than using passwords.
- Disable Password Authentication: Once you’ve set up public key authentication, disable password authentication to further enhance security.
- Configure Firewall Rules: Make sure your firewall is configured to allow SSH traffic on port 22 (or whatever port you’re using).
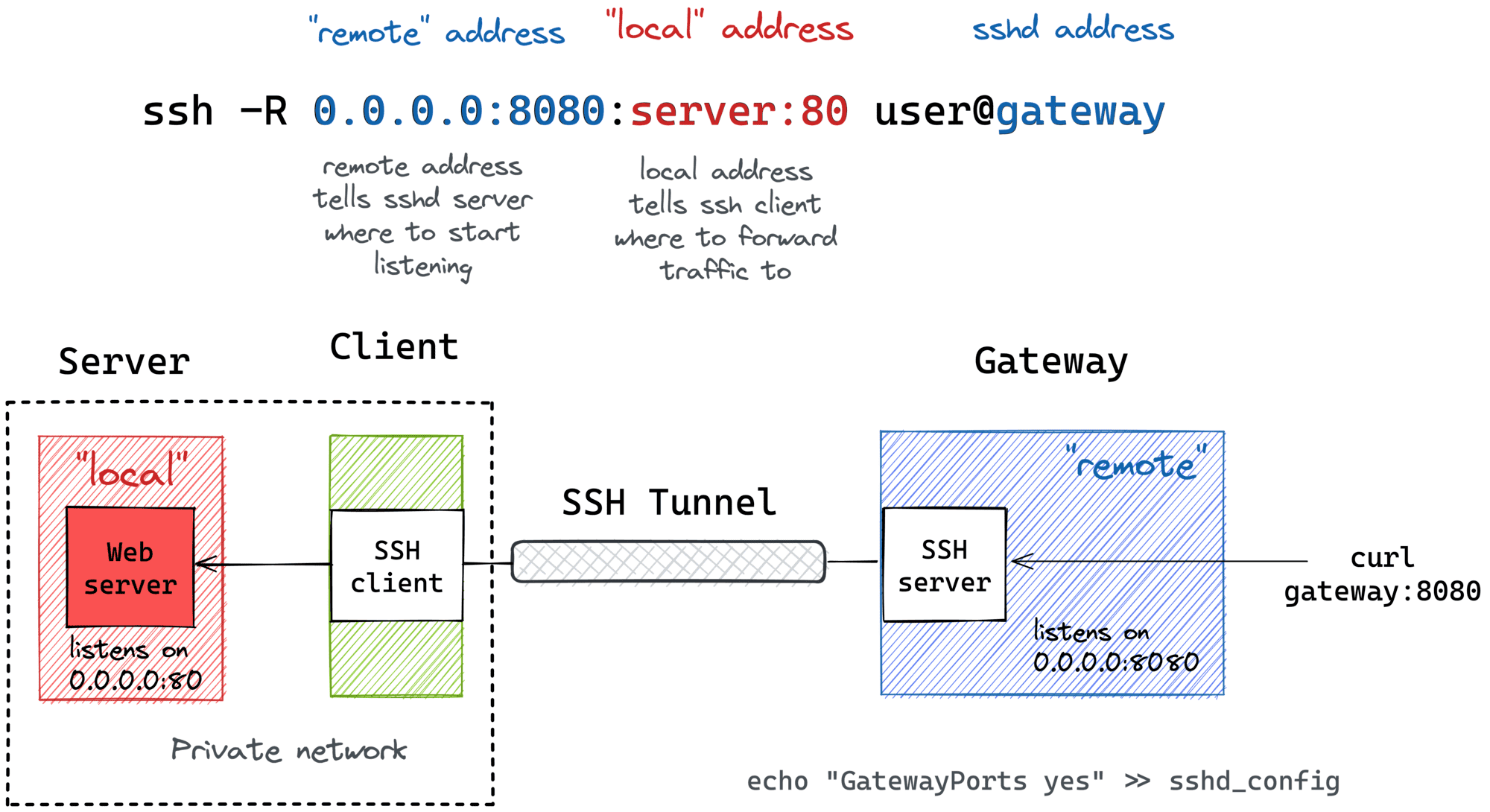
Example Implementation of SSH RemoteIoT
Let’s take a look at a real-world example of how SSH RemoteIoT Example can be used. Imagine you’re a developer working on a smart home project. You’ve got a fleet of IoT devices scattered throughout the house, and you need to manage them remotely. Here’s how SSH can help:
Step 1: Set Up SSH on Your Devices
Install SSH on each of your devices and configure it to use public key authentication. This will ensure that only authorized users can access your devices.
Step 2: Connect to Your Devices
Using a terminal or command prompt, connect to each of your devices and start managing them remotely. You can execute commands, transfer files, and even monitor device performance—all from the comfort of your desk.
Step 3: Automate Tasks
Once you’ve got SSH set up, you can start automating tasks to make your life easier. For example, you could write a script that automatically updates all your devices at once, saving you time and effort.
Real-World Applications
SSH RemoteIoT Example has a wide range of applications in the real world. Here are just a few examples:
- Smart Homes: Use SSH to manage smart thermostats, lights, and security systems.
- Industrial IoT: Use SSH to monitor and control industrial equipment from anywhere in the world.
- Agriculture: Use SSH to manage sensors and devices used in precision agriculture.
Security Considerations
While SSH is incredibly secure, there are still a few things you need to keep in mind to ensure your devices are fully protected. Here are some security considerations to keep in mind:
- Use Strong Passwords: Even if you’re using public key authentication, it’s a good idea to use strong passwords as a backup.
- Disable Root Login: Disabling root login can prevent attackers from gaining full control of your devices.
- Monitor Logs: Regularly check your SSH logs for signs of unauthorized access attempts.
Best Security Practices
Here are a few best practices to help you keep your SSH connections secure:
- Use Public Key Authentication: This is much more secure than using passwords.
- Limit Access: Only allow trusted IP addresses to connect to your devices.
- Keep Software Updated: Regularly update your SSH software to ensure you have the latest security patches.
Common Issues and Solutions
Even with the best tools and practices, things can sometimes go wrong. Here are some common issues you might encounter when using SSH RemoteIoT Example, along with solutions to help you fix them:
- Connection Refused: Make sure your firewall is configured to allow SSH traffic on port 22.
- Authentication Failed: Double-check your public key and make sure it’s correctly configured on your device.
- Slow Connections: Try optimizing your network settings or switching to a faster internet connection.
Troubleshooting Tips
Here are a few tips to help you troubleshoot SSH issues:
- Check Logs: Look at your SSH logs for clues as to what might be causing the issue.
- Test Connectivity: Use tools like ping or traceroute to test connectivity to your device.
- Reboot Devices: Sometimes a simple reboot can fix connectivity issues.
Best Practices for SSH RemoteIoT
To get the most out of SSH RemoteIoT Example, it’s important to follow best practices. Here are a few tips to help you manage your IoT devices securely and efficiently:
- Automate Tasks: Use scripts to automate repetitive tasks, saving you time and effort.
- Monitor Performance: Regularly check the performance of your devices to ensure they’re running smoothly.
- Keep Software Updated: Regularly update your SSH software to ensure